Margin Research Blog
Musings, insight, and hot takes on Security, Research, and Technology from the Margin Research team.
We know how to detect XZ and we know how to solve it
Security posture is relative. It is improper to designate something as perfectly secure, and anyone who claims otherwise is selling you something. We achieve a degree of security that lets us sleep at night by creating the most challenging maze possible for any would-be attackers. This strategy, often referred to
Same Same, but Different
What the i-Soon leak reveals about the Chinese offensive cyber capability industry.

Russia’s largest hacking conference: Biggest hits from Positive Hack Days 2023
Russia’s largest hacking conference, Positive Hack Days, recently took place in Moscow from Friday, May 19 to Saturday, May 20. The event was held at Gorky Park, a large park and cultural complex in Moscow, and split into an area freely open to the public and a village area
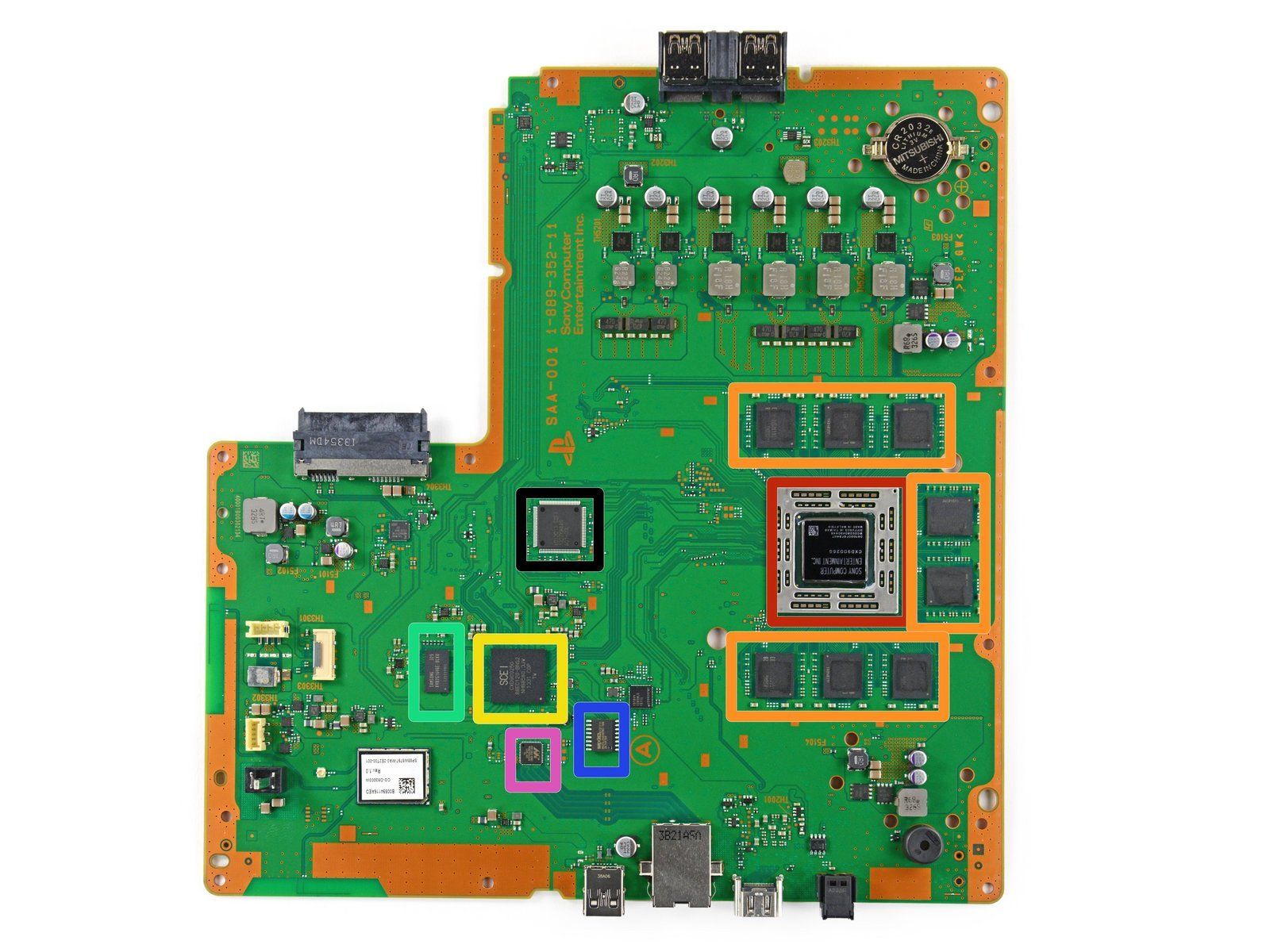
Emulating and Exploiting UEFI Firmware
One major difficulty of doing low-level security research is the lack of a testing and debugging environments. When testing regular userspace programs written in C and other high-level programming languages, there are a plethora of debugging tools like gdb to run, inspect, and modify a running process. Dynamically inspecting software

Entity Resolution in Reagent
One of the biggest challenges in many modern technologies is Entity Resolution, the practice of figuring out when two separate entities are actually the same thing, such as Git contributors. We leverage LLMs in our graph databases to solve this problem for GitHub contributors and more!

Analyzing Russian Internet Firm Yandex, Its Open-Source Code, and Its Global Contributors
Russian internet company Yandex has been in the news recently, and not just because it’s one of the leading and most globally reaching technology firms in Russia. The company, founded as a search engine in 2000 and now worth billions of dollars, announced plans in November 2022 to potentially

DGraph Post-Mortem Analysis
Margin Research’s Social Cyber project was originally hosted on a graph database (DB) technology called DGraph. In an unfortunate turn of events, DGraph ceased to exist as a company, requiring the Margin Research team to migrate our analysis tool to a different graph DB: Neo4J. This brought the question
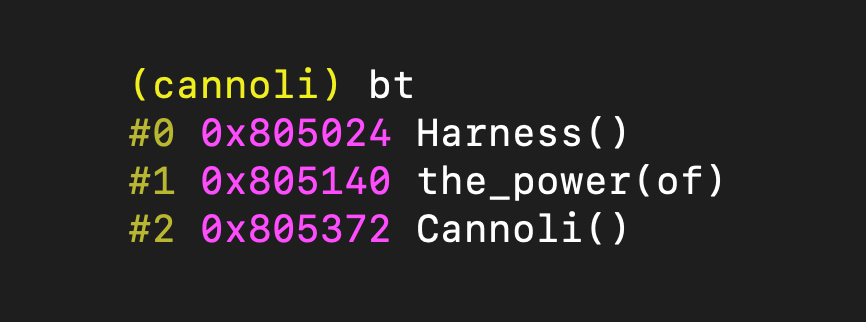
Harness the Power of Cannoli: Implementing a Program Backtrace
So, you’ve heard about Cannoli, the high-performance tracing engine, but don’t know where to start. Perhaps you read the source code but don’t understand how to implement your analysis. Or maybe you’re someone who learns by example and finds inspiration in detailed walkthroughs. If so, this

Analyzing Russian SDK Pushwoosh and Russian Code Contributions
Reuters recently reported on November 16 that Pushwoosh, the maker of a software development kit (SDK), was falsely representing itself as an American company when in fact the technology company is based in Russia. Its code is reportedly used in thousands of Apple and Google app store applications, and the