Resources
Dive into the latest and greatest presentations, whitepapers, and publications from the Margin Research team.

Mobilizing Cyber Power: The Growing Role of Cyber Militias in China’s Network Warfare Force Structure
Over the past decade, the People’s Republic of China (PRC) has undertaken a sweeping reform of its cyber reserve forces, transforming its cyber militia system from a peripheral asset into a strategically relevant component of the People’s Liberation Army’s (PLA’s) broader cyber warfare architecture. Within China,

China's Health Sector Ambitions and Information Needs: Implications for U.S. Health Care Cyber Defense
Cyber vulnerabilities involve risk management; perfect cybersecurity is impossible with currently deployed technologies. At present, it is therefore impossible to defend against all Chinese, state-backed or non-state-backed cyberattacks on the health care sector. China’s ever-expanding arsenal of potential methods for cyberattacks is too sophisticated to be completely blocked. It

China’s Cyber Laws and Regulations
China’s President Xi Jinping has made a point of emphasizing the importance of law in China and the promotion of the rule of law at the base of Chinese Communist Party governance and power. Like any law, Chinese law expresses national policy. In China, management and control of cyberspace

China’s Cyber Operations: The Rising Threat to American Security
At present, China’s cyber capabilities and operations have increased exponentially to the point where they pose a highly significant national security threat to the United States and all China’s perceived adversaries.
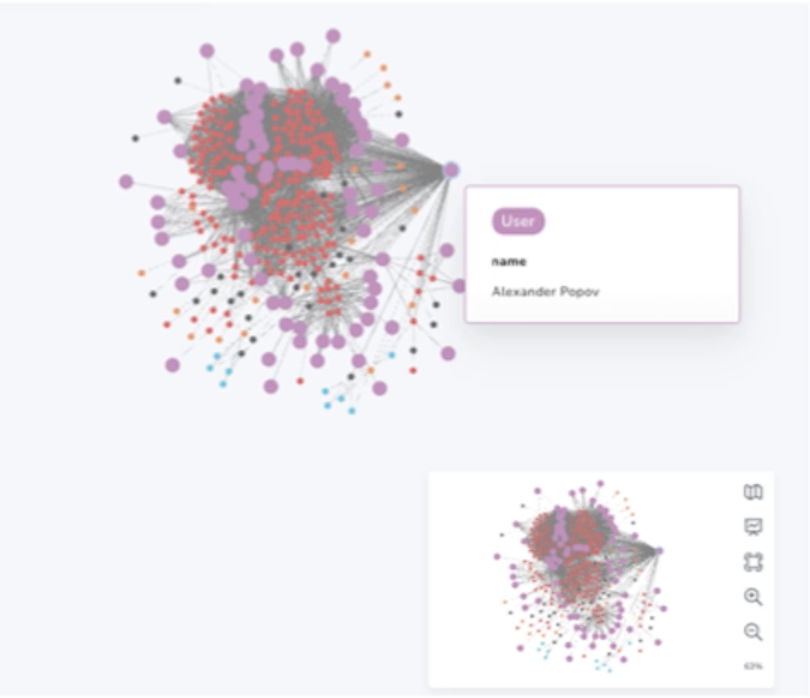
Russia’s Cyber Operations are a Threat to American National Security
Document summarizing a larger research paper outlining the threats and structure of Russian cyber operations.

Russia’s Open-Source Code and Private-Sector Cybersecurity Ecosystem
When analyzing Moscow’s cyber power, much of the policy community and international media focus on the Russian government’s internal cyber units and several criminal entities identified in the press. This overlooks a vast part of the Russian cyber ecosystem—including open-source code projects to which Russian developers contribute

Pulling Mikrotik Into the Limelight
Pulling MikroTik into the Limelight presentation deck as presented at RECon Montreal 2022 by Ian Dupont and Harrison Green. In the wide expanse of router manufacturers and models, there is one reverse engineering target that stands out from the rest: MikroTik. Unlike many routers which run a patchwork of services
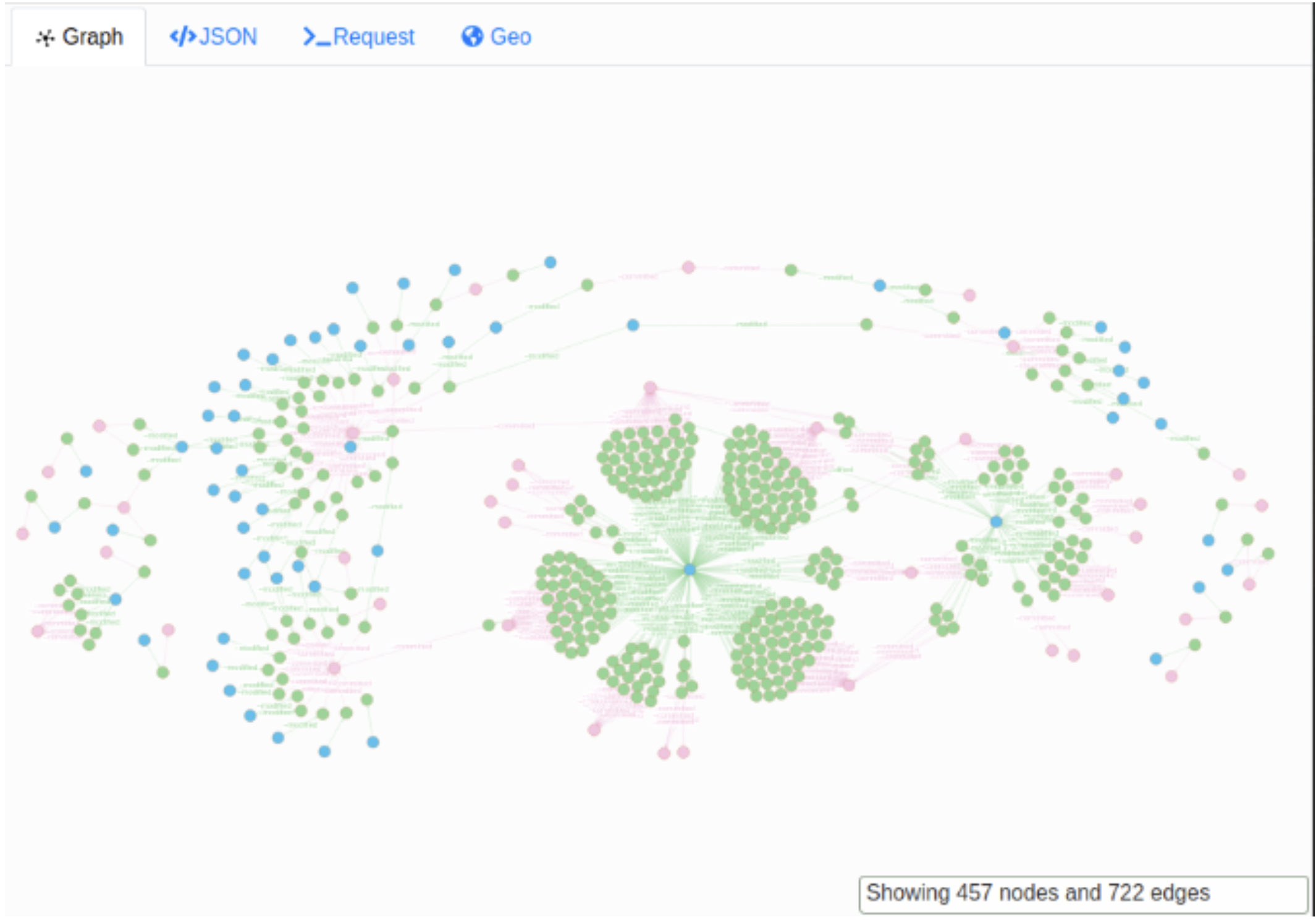
Who Owns Your Kernel?
Presented at Summercon 2021, we discuss the open source supply chains, information operations targeting them, and how to identify these attacks (with some crazy examples of course). This project, to explore and protect the integrity of open source code, was funded via DARPA's SocialCyber program.

In Search of Lost Bytes: Hardware Implants and the Trouble With Supply Chains
Digital markets have quickly grown to international proportions, complexities in materials, development, and distribution have developed accordingly, resulting in market efficiency and, often overlooked, incalculable risks. There is a fine line between acceptable and irreconcilable risk, while some risks are mitigatable, others are not, and ignoring the facts has disproportionate

Firmly Rooted in Hardware
Practical protection from firmware attacks in hardware supply chain. This talk reviews the practical risk from supply chain attacks, with a focus on those that may impact firmware integrity, either through hardware implants or other threats to firmware during manufacturing, provisioning, or deployment. Fresh styles and latest trends in hardware

Huawei and the Third Offset
In order to effectively mitigate the security risks posed by Huawei, the U.S. Department of Defense needs to fund and integrate cutting-edge technologies from the private sector. Although concern over Huawei’s implications for national security remains high, current U.S. strategies against Huawei have largely been framed as
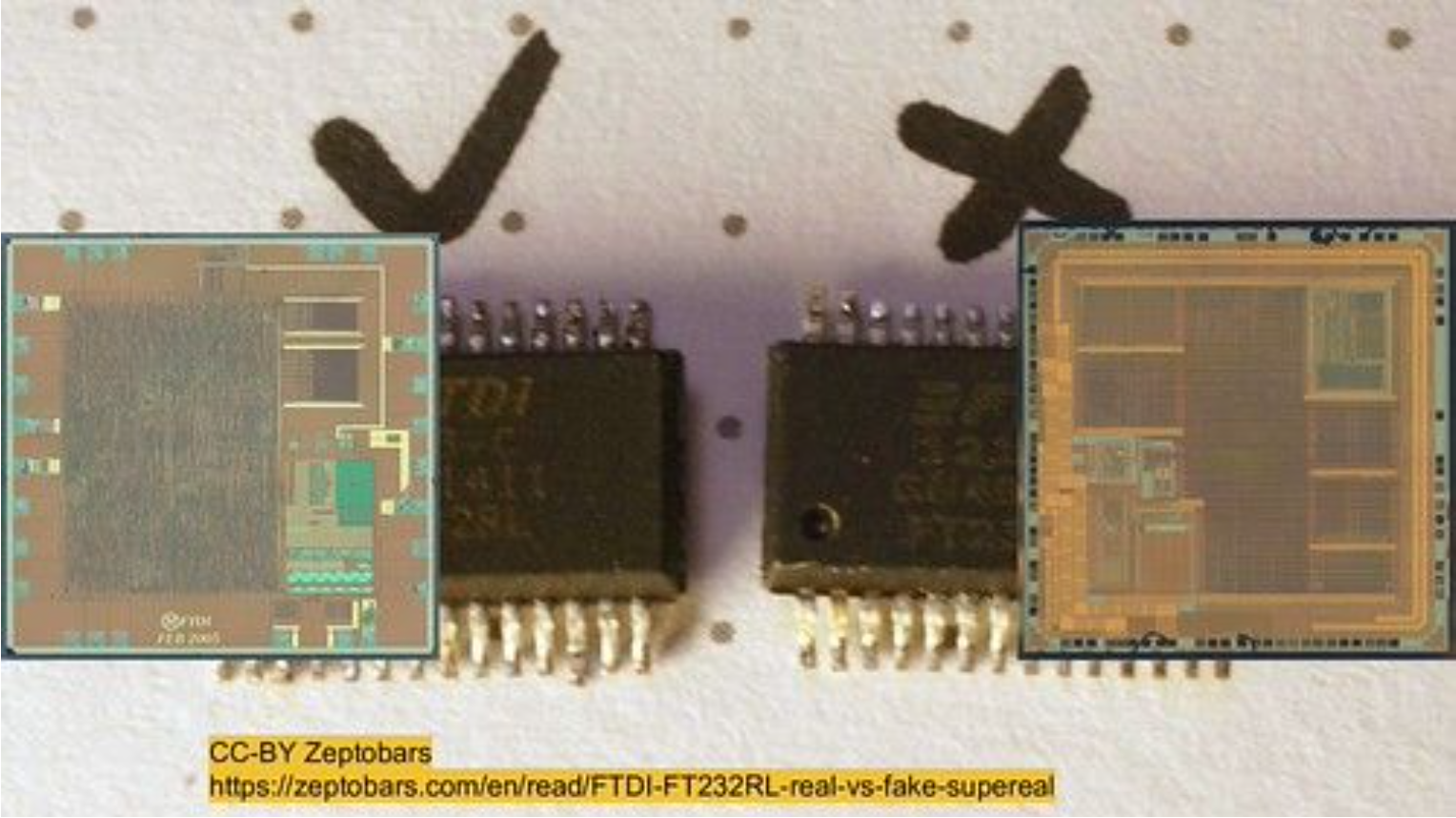
The Secret Life of Supply Chains
A presentation by Sophia d'Antoine at the 2019 COUNTERMEASURE IT Security Conference in Ottawa, Canada. Last year, Bloomberg’s Big Hack article gave everyone a much needed scare which forced companies to evaluate their exposure to supply chain intervention attacks. But a wider acknowledgment of the problem doesn’

In Search of Lost Bytes: Assurance Under Low Trust Conditions
Digital markets have quickly grown to international proportions, complexities in materials, development, and distribution have developed accordingly, resulting in market efficiency. When expanding any supply chain for an IoT voting machine to an entire national infrastructure, cost, reliability, and security of the alien component is taken into account. However, often

The Risks of Huawei Risk Mitigation
While there is widespread agreement that Huawei devices in 5G infrastructure pose risk to the U.S. and allied nations, the policy community has paid insufficient attention to the technical aspects. This article attempts to rectify this gap.

Hacking the Motherboard: Exploiting Implicit Trust in All of the Forgotten Places
Our economy is becoming more specialized and more and more tasks are being automated. We must have confidence in these systems. However, this confidence relies on too much implicit trust – overlooking serious risks. Assurance in this area is hard won, manual, and costly.