Executive Summary
As China's "decade-long quest to become a superpower" comes to fruition, the PRC has increasingly moved to eliminate barriers between its civilian-commercial industries and the State. Companies within the technology industries, particularly domestic cybersecurity enterprises, increasingly stand at the forefront of their fields, offering insight and services that are not only unparalleled in their scope, but that also represent a tremendous potential resource for China's government and military. For those interested in the development of China's political and military strategy, understanding China's domestic cybersecurity ecosystem is critical.
China's cybersecurity industry has developed rapidly, with experts moving from positions in larger tech firms to establish companies of their own, often maintaining their earlier connections. These firms operate under increasingly restrictive government policies.
This article presents an introductory survey of selected Chinese cybersecurity firms (see table below), providing their areas of focus, the backgrounds of their founders, and (some of) their partners and investors. Most of these firms focus on vulnerability research, threat detection, and security intelligence, and their services and products offer their clients protection from offensive cyber activities. A growing number of these firms also focus on blockchain security. While their investors are predominantly Chinese venture capital firms, these companies service clients and maintain partnerships around the globe.
Introduction
In late February 2022, a PRC cybersecurity team, Qi An Pangu Lab, published a report [English | Chinese] linking an exploit targeting the Linux platform to the U.S. National Security Agency (NSA). A few months earlier, a team from the lab placed second in the Tianfu Cup, a hacking competition hosted in China, where participants were able to exploit weaknesses in software code, known as vulnerabilities, to infiltrate Windows 10, Adobe PDF Reader, Ubuntu, Apple iOS 15 and Safari, and Google Chrome, among several other companies. (These competitions are an integral part of a healthy and flourishing cyber industry in any country. Teams that participate in network security competitions typically share exploits with the software and hardware providers so that the companies can then fix any vulnerabilities.)
Pangu Lab is a cybersecurity research team under Pwnzen Infotech Ltd., a company founded by a team of veterans in information security and vulnerability exploitation. The firm was backed in its early days by Qihoo 360, a behemoth in China’s cybersecurity industry and has collaborated closely with Qi An Xin (奇安信), another major cybersecurity firm founded by Qihoo 360’s founder Qi Xiangdong.
Pangu Lab is merely one among a multitude of cybersecurity research firms that have emerged in China’s technology market over the past decade. Cybersecurity professionals interested in the development of China’s cyber industry have long focused on macro-level developments in the law, government ministries, and leading industry enterprises. But as the country’s technology enterprises have matured, researchers and engineers employed in China’s cybersecurity industry have increasingly used their expertise and experience from working in tech conglomerates to form their own firms, creating a growing and thriving cyber ecosystem. This ecosystem is increasingly used by the People’s Liberation Army (PLA), security services, and policymakers to support their cyber operations.
Those interested in Chinese cyber policy and the trajectory of the nation’s cyber industry should pay close attention to the proliferation of firms engaged in cybersecurity research. As part of its military-civil fusion (MCF) approach, China’s leadership has emphasized the need to foster innovation in domestic technologies and has called on private enterprises to contribute to the security of the State and its citizens. Institutions and individuals embedded in China’s cybersecurity industry have stressed that start-ups and smaller firms are a critical source of this innovation in network security. These companies, along with and under the guidance of China’s tech giants, have played and will continue to play a formative role in the development of China’s national cyber strategy.
Rapid Growth of Chinese Cyber Tech
While their direct engagement with government authorities varies, China’s cybersecurity firms operate under increasingly rigid constraints. Zhou Hongyi, one of Qihoo 360’s founders, has been vocal in touting the strategic benefits of keeping knowledge of vulnerabilities close to home, noting that vulnerabilities are no longer of use once exposed publicly by Chinese hacking teams at competitions. Cognizant of this fact, China has discouraged its security researchers from participating in hacking competitions abroad, particularly those where zero-day vulnerabilities may be publicly disclosed.
Those researchers that are approved to attend must disclose any discovered vulnerabilities to the government ahead of time. Recent regulations also mandate that individuals and companies within China share zero-day vulnerabilities with the government within 2 days of discovery. Vulnerabilities shared in hacking competitions within the PRC can and have been exploited by government hacking campaigns to infiltrate software and hardware providers, such as Google and Apple, before they can be patched. They have also been used to target individuals belonging to vulnerable populations, such as Uyghur Muslims.
As the country’s cyber capabilities improve at an unparalleled pace, maintaining ties with China’s tech industry is critical not only for technological and economic advancement but also for cybersecurity purposes. Experts in China stand at the forefront of vulnerability research and have strong insight into the offensive and defensive techniques necessary to combat potential infiltration and exploitation. Cutting off the exchange of knowledge between U.S. and Chinese cyber industries would undermine the ability of service providers to protect their products and network infrastructures and would also undercut visibility into changing developments in hostile cyber activities. But domestic cyber enterprises, as in most countries, also play a vital role in providing infrastructure, talent, and resources to State operations, sometimes by choice, sometimes under legal and political pressure.
Industry leaders in China, such as Tophant's CEO Chen Xie, see China's cybersecurity "universe" as unique and expect growth to continue to outpace overseas counterparts. According to Xie, cybersecurity firms, particularly those dealing with personal data security, zero trust, cloud security, and privacy, are more likely to receive funding from the government, state-owned enterprises, and publicly listed companies when compared with other industries.
Analysts interested in the development of China's cybersecurity industry and national cyber strategy would be remiss to neglect investigating the make-up and distribution of local firms. Understanding this rapidly evolving technology base is critical to U.S. cybersecurity efforts.
Industry Leaders and Internet Giants
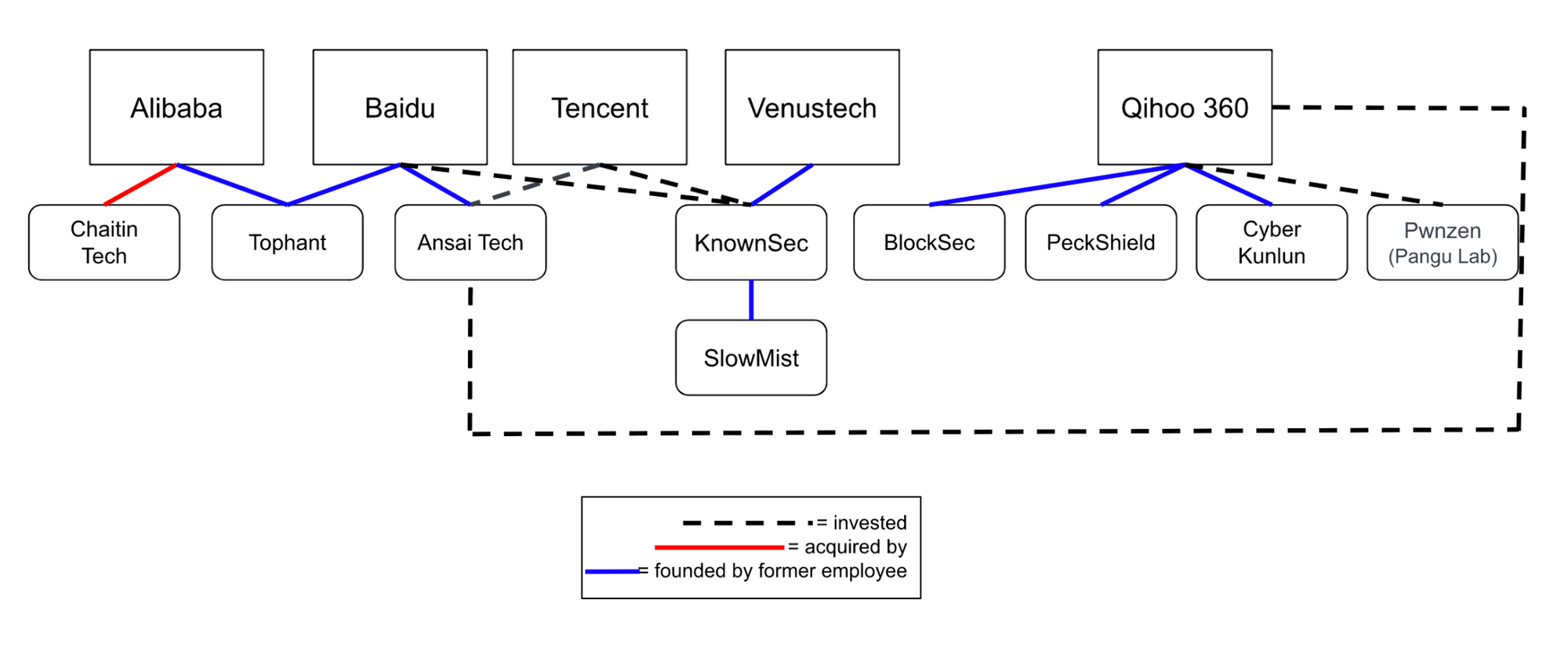
China’s major tech firms, by virtue of their size and status within the industry, often work closely with the government to advance the PRC’s cyber strategy. Several established cybersecurity companies, for example, have partnered with local authorities and universities to service China’s National Cybersecurity Center (NCC) and establish research facilities at the site, including Qi An Xin, TopSec, Tencent, Huawei, Integrity Tech (北京永信至诚科技), Qihoo 360, NSFocus, and DeepBlue AI (深兰科技). US officials have accused TopSec, along with Qihoo 360, of providing talent and services to the PLA, and the firm was linked in 2013 to the hack of the health insurance company Anthem. Venustech, Huawei, Alibaba, Baidu, Qihoo360, NSFocus, TopSec, Qi An Xin, Integrity Tech, and Tencent have all sponsored the Tianfu Cup hacking competition, along with other organizations.
Qihoo 360’s coordination with government authorities is particularly notable. The company delisted from the New York Stock Exchange in 2016 and re-listed in China to improve its access to PRC government and military contracts. It has since cultivated close ties with the government. Qihoo 360 was placed on the U.S. Department of Commerce's Bureau of Industry and Security (BIS) Entity List in 2020.
Qihoo 360 has also been linked to COSEINC, a Singapore-based exploit broker that was placed on the Entity list in 2021 for "malicious cyber activities." Thomas Lim, COSEINC's founder, established the SyScan hacking conference in 2004. Qihoo 360 began sponsoring the conference in 2012 and purchased the brand from Lim in 2015, changing the name to SyScan 360. (COSEINC's founder, Thomas Lim, was also known to have cooperated with Pangu Lab and was often invited to speak at MOSEC, a mobile security conference organized by Pangu and sponsored by several organizations, including Venustech (2015-2019), Huawei (2019-2021), Ant Group (2016-2021), Cyber Kunlun (2021), Qi An Xin (201-2021), Baidu (2017-2021), Qihoo 360 (2015-2019), and Microsoft (2016). The conference has also partnered with KnownSec and Tencent.)
CloverSec (四叶草安全) is another well-known company that helps to organize a number of security conferences and hacking competitions, including the Tianfu Cup. The firm specializes in vulnerability detection and protection and also has close ties to government authorities. Its founder, Ma Kun (马坤), was a well-known member of Honker Union (HUC, 中国红客), an early hacking collective that emerged in response to the U.S. bombing of the Chinese embassy in Belgrade, and became famous for infiltrating the video game company Blizzard Entertainment. Ma Kun started the company after working to detect vulnerabilities for CNCERT, a “non-government non-profit cybersecurity technical center” responsible for China’s cybersecurity emergency response community. (The firm’s investors include Ant Group, an affiliate company of Alibaba that deals with fintech.)
Many cybersecurity professionals in China get their start working for established firms like the ones above and then leave to form their own companies, taking with them years of experience and expertise in vulnerability and other security research. Others gain experience and develop personal networks from participating in security research competitions before venturing into the professional industry. Regardless of their origin, many of these firms are often backed and supported by one or more of the larger tech conglomerates. (Qihoo 360 is particularly committed to fostering growth in the security market to promote a safe security ecosystem.) The companies below represent a small sampling of the breadth of cybersecurity research and development enterprises in China’s technology market.
Example Chinese Cyber Firms
Tophant (斗象科技)
Founded: 2014
Investors: Eastern Bell Capital, Shenzhen Hui Capital Limited, Cowin Capital, Yinxinggu Capital, Linear Capital, China Electronics Technology Group, Spinnotec, Xiamen C&D Corporation, Zhangjiang Hi-Tech Investment, Qianhai FOF
Online presence: Website | Weibo
One of the leading cybersecurity firms in the country, Tophant offers cybersecurity testing, monitoring, and data analysis for government enterprises, as well as clients in finance, entertainment, e-commerce, and other industries. Prior to starting Tophant, Chen Xie (谢忱), the current CEO, was employed as a Network Security Expert at Alibaba and Baidu, and he now serves as an external expert to the China Academy of Information and Communications Technology, a research institute under the Ministry of Industry and Information Technology (MIIT). Tophant’s investors also include the China Electronics Technology Group (CETC), a PRC state-owned company.
Tophant provides support to CNCERT, as well as China’s National Information Security Vulnerability Sharing Platform (CNVD), and acts as an Advanced Support Unit for Shanghai’s municipal network security. The firm has collaborated with State ministries, such as the Ministry of Public Security (MPS), to conduct research into vulnerability mining and offensive and defensive techniques. Tophant also hosts Freebuf, an online forum for cybersecurity professionals and hackers.
Cyber Kunlun (赛博昆仑)
Founded: 2021
Investors: CICC Capital, Hike Capital, Sequoia Capital China, ZhenFund
Online presence: Website
Cyber Kunlun is well-known for winning first place in the Tianfu Cup. (The company also helps organize the event.) Its founder and CEO, Wenbin Zheng (郑文彬, mj0011), formerly served as the Chief Technology Officer of Qihoo 360 and during his tenure established the infamous 360 Vulcan research team, known for their exploits at Pwn2Own, an international hacking competition based in Canada. Xuebin Chen (陈雪斌), Cyber Kunlun’s Chief Technology Officer, also worked as a director at Qihoo 360’s Vulnerability Research institute.
Cyber Kunlun’s researchers are at the forefront of vulnerability research, with a stated focus on providing exclusive defense capabilities for zero-day vulnerabilities. Vulnerabilities, according to Zheng Wenbin, are the core of offense and defense in cybersecurity, as hackers need to first obtain vulnerabilities if they want to attack a company. Zheng also notes that supporting affected enterprises by sharing discovered vulnerabilities is “one of [the] key[s] to a good research team. Cyber Kunlun has identified and reported dozens of vulnerabilities in Windows, iOS, Google, open-source, and VMware products. (Of Microsoft’s 145 vulnerability fixes from April’s Patch Tuesday, 36 were reported by Cyber Kunlun, including half of the 10 critical vulnerabilities.)
The firm maintains close ties with Qihoo 360 and has recently partnered with the aforementioned Pangu Lab to coordinate their respective teams’ knowledge in vulnerability mining and protection and advanced threat detection and response to develop new security products and services.
Chaitin Tech (长亭科技)
Founded: 2014
Investors: ZhenFund, Matrix Partners China, Junsan Capital, Qiming Venture Partners, Apple Funds, Didi Global, Peakview Capital (China)
Online presence: Website | Weibo
Chaitin Tech’s founders have similarly impressive backgrounds. Wenlei Zhu (朱文雷), Kun Yang (杨坤), and Yusen Chen (陈宇森) met as members of the Blue Lotus hacking teams, known for their exemplary performance in the DEFCON CTF competitions before deciding to form a business together. Chen now sits on the board of Saitech, a Singapore-based bitcoin mining operation, and also founded Hangzhou Jiao Gei Mao Ba Technology, which specializes in the application of AI to gaming.
Chaitin Tech's team has won multiple domestic and foreign network security competitions and provides infiltration testing and security consulting services to a wide range of customers. It also hosts its own CTF competition, with questions designed from the modification of real-world software. This impressive performance has earned its founders the “favor and recognition” of the Cyberspace Administration of China, MIIT, and MPS. Clients include DiDi Chuxing, Tencent, Bank of China, Agricultural Bank of China, China Merchants Security, Douyin, China Southern Airlines, Unilever, Huawei, Panasonic, Vivo, China Mobile, and VIPKid, among many others.
The startup was acquired by Alibaba Cloud in 2019 but has been allowed to continue to run independently.
BugBank (漏洞银行)
Founded: 2012
Investors: Puhua Capital, SB China Capital, NewMargin Ventures
Online presence: Website | Weibo
Bugbank, an internet security service platform under Shanghai Moule Network Technology Co., Ltd., operates an automated vulnerability diagnosis system and has accumulated a database of vulnerabilities following years of research. Its founders, including Xiaonan Bao (鲍晓南), CTO Xuesong Zhang (张雪松), and CEO Luo Qinglan (罗清篮), developed the database as means to bring together white hat hackers and domestic enterprises in an effort to better coordinate emergency responses to vulnerabilities and exploitation risks. BugBank was designed and operates under the philosophy that cooperation between actors in the domestic security industry is better for security than competition.
Bugbank employees have strong backgrounds in information security. The BugBank Red Team consists of 30,000 network security experts with experience in a variety of areas, including “hacking” and “cracking.” The founding team, prior to creating Moule, provided vulnerability discovery and detection services for the 2008 Beijing Olympics. CEO Luo Qinglan personally began hacking at a very young age after experiencing the “first hacker war” - an incident in 1999 where American and Chinese hackers exchanged a series of cyber attacks after the U.S. bombed a Chinese embassy in Belgrade. As a student in high school and college, he worked as a white hat hacker and won several awards for his work in network security.
The company coordinates with a variety of partners at differing levels of cooperation. Their strategic partners include various departments within the Shanghai government, the Chinese National Vulnerability Database (CNNVD), and the Open Web Application Security Project (OWASP). Bugbank also maintains "friendship links" with Baidu and TopSec, in addition to several other security companies.
KnownSec (知道创宇)
Founded: 2007
Investors: China Internet Investment Fund, Tencent, Baidu
Online presence: Website | Twitter | Github | Weibo | Website ( Blockchain Lab) | Medium (Blockchain Lab) | Twitter (Blockchain Lab) | Weibo (Blockchain Lab) | Zhihu (Blockchain Lab) | Medium (404 Team) | Youtube (404 Team) | Weibo (Research Team)
Wei Zhao (赵伟), one of KnownSec’s founders, worked as a security researcher at Venustech and McAfee Security Lab prior to starting the company. The firm has grown to encompass 3 research and development centers in Beijing, Chengdu, and Wuhan, with branches in several other cities. Over 1800 employees work for the company in a variety of areas.
KnownSec's brands approach information security from a number of facets. The 404 Lab is a relatively well known team that has uncovered several vulnerabilities in network systems, including Microsoft, Oracle, and Apple. ZoomEye is an internet-scale network scanner that maps cyberspace. Seebug is a vulnerability database where hackers can submit vulnerabilities for rewards. POCSuite3 is a framework to verify and exploit vulnerabilities. Ceye.IO is a tool for monitoring the Domain Name System (DNS) and “can help security researchers collect information when testing vulnerabilities.” KnownSec even hosts its own hacking competition, known as KCon.
KnownSec provides services to the Party, government, military, and private enterprises, as well as citizens. Customers include the Cyberspace Administration of China, MIIT, MPS, the State Administration for Market Supervision, China Merchants Group, China Communications Construction Company, China General Nuclear Power, WeChat, Douyin, and Weibo. In 2021, KnownSec was selected to serve as a National Network Security Emergency Service Support Unit for CNCERT.
Because KnownSec believes that “there is no national security without cybersecurity,” the firm has committed to following Party leadership, established a Party branch in 2012, and organized a security team composed of party members. The company website states that “the essence of network security is confrontation, and the essence of confrontation is the ability to compete on both ends of the offensive and defensive.”
Ansai Technology (安赛科技)
Founded: 2012
Investors: Tencent, Qihoo 360
Online presence: Website
Ansai Technology was founded by Lin Yujian (林榆坚), who previously worked as a network security researcher at Baidu. They are also known by the moniker AISec, which stands for Artificial Intelligence Security. The company focuses on research in threat detection technologies, including data analysis, vulnerability mining, and intrusion detection. They are known for their vulnerability scanning product, AIScanner, and WebIDS, a version of AIScanner that serves as an Internet vulnerability and intrusion detection system. Ansai also uses their technology to maintain a platform for analyzing and monitoring advanced persistent threats (APT).
Although their customers are far too many to list, Ansai has provided services for several large tech companies, government ministries, and information security authorities, including Qihoo 360, Huawei, Baidu, the National Research Center for Information Technology Security, the China Information Technology Security Evaluation Center, CNERT/CC, the China Academy of Information and Communications Technology, the Ministry of Public Security, the Ministry of Culture, the Ministry of Science and Technology, and the Ministry of Industry and Information Technology.
Ansai Technology is certified by the Ministry of Industry and Information Technology as a National Information Technology Talent Training Base, a certification established as part of China’s strategy to foster domestic talent in critical technologies. The company also serves as a technological support unit for the National Vulnerability Database (CNNVD), operated by the China Information Technology Security Evaluation Center (中国信息安全测评中心), “a state agency that provides cybersecurity services to the PRC government and large Chinese corporations.”
SlowMist (慢雾科技)
Founded: 2018
Shareholders: Chenming Zhong, Qi Wu (吴琦/Chairman), Weipeng Huang (黄伟鹏), Bi Huang (黄比)
Online presence: Website | Medium | Twitter | Weibo | Github |Github (evilcos) | Blog (evilcos) | Twitter (evilcos) | Weibo (evilcos) | Zhihu (evilcos)
SlowMist, a blockchain security firm, was founded by former KnownSec VP Chenming Zhong (钟晨鸣, handles: cosine/余弦/evilcos). Zhong is a "well-known hacker" from the xeye team who created KnownSec’s ZoomEye, led the 404 team, and founded the company Joinsec. Zhong maintains that the primary values of SlowMist are, in order of importance, don't be evil, don't have a poor attitude, and approach network security with a sense of reverence.
SlowMist quickly became well-known for reporting several previously unknown and undisclosed vulnerabilities during the March 2018 Ethereum Black Valentine’s Day event. The company now offers security services to thousands of customers, including security auditing, threat intelligence, and other consulting. Their products include anti-money laundering software, a vulnerability scanner, Crypto hack archives, and a smart contract firewall.
SlowMist has worked on a number of projects, including Huobi, Binance, Crypto.com, EOS, and Amber Group, and partnered with several international companies, such as Amazon Web Services, Cloudflare, Bitdefender, and FireEye.
Per the company website, SlowMist has "actively participated" in promoting blockchain security standards. They were one of the first to join the MIIT working group for the "2018 China Blockchain Industry White Paper" and are a member of the "Joint Laboratory of Blockchain and Network Security Technology" in the Guangdong-Hong Kong-Macao region.
BlockSec
Founded: 2021
Investors: Fenbushi Capital, A&T Capital, Qulian, Impossible Finance, Incuba Alpha, Near MetaWeb Ventures
Online presence: Website | Medium | Twitter | Zhihu
A very young company, BlockSec primarily focuses on blockchain security and governance through the development of platforms that help to monitor cryptocurrency and related interactions, such as providing smart contract transaction auditing. BlockSec lists among its clients Amber Group, Ant Group, Burrow, Crypto.com, Impossible Finance, and Tidal Finance.
The firm was founded by Yajin Zhou (周亚金) and Lei Wu (吴磊), who both worked at Qihoo 360 as security researchers prior to starting the company, and who both currently work as professors at the School of Cyber Science and Technology and the College of Computer Science and Technology at Zhejiang University. Yajin Zhou’s research interests include “software security, operating systems security, hardware-assisted security and confidential computing,” particularly in the areas of smart contracts and decentralized finance.
PeckShield (派盾科技)
Founded: 2018
Investors: Gaorong Capital
Online presence: Website | Medium | Twitter | Zhihu | Weibo
Another firm focused on blockchain security, PeckShield was founded in 2018 by BlockSec's founder Lei Wu, Xuxian Jiang (蒋旭宪), a former Chief Scientist with Qihoo 360, and Chiachih Wu (吴家志), also a senior security researcher at Qihoo 360. Jiang also served as a PhD advisor to Wu, Lei, and Yajin Zhou while working as a professor at North Carolina State University.
PecksShield touts the substantial experience of its employees, who have worked as "seasoned security professionals and senior researchers... at companies such as Qihoo 360, Microsoft, Intel, Juniper, and Alibaba" and are known for their achievements in “vulnerability analysis, operating systems, and malware defense.” The company aims to use its team's extensive experience in security research to analyze risks in public blockchains to develop responses to risks that clients may face. To help clients prevent hacking attacks, PeckShield developed a platform, DAppShield, that allows clients to conduct security testing and monitor funds. The firm offers products to manage and monitor digital assets. Clients primarily include blockchain infrastructure vendors, crypto wallets, and exchange companies, such as Bitpie, KuCoin, and Newdex.
Conclusion
China has a small but growing ecosystem of private companies doing cybersecurity work in a variety of emerging domains. This survey shines a light on this growth and provides an informative exploration of the growth in the Chinese cybersecurity industry, focusing particularly on links between individuals and organizations as well as funding sources. One notable finding is a strong movement by penetration testing companies towards securing blockchain technologies which parallels shifts in the US domestic market.