Margin Research Blog
Musings, insight, and hot takes on Security, Research, and Technology from the Margin Research team.

Better Analyzing Foreign Adversary Threats to Open-Source Software
Global contributions to open-source software (OSS) add tremendous value: for years, they have forged connections between developers around the world, enabled dispersed and specialized talent to build better software for users, and collectively helped ensure that OSS remains available, updated, and relevant for users everywhere. Having more eyeballs on code
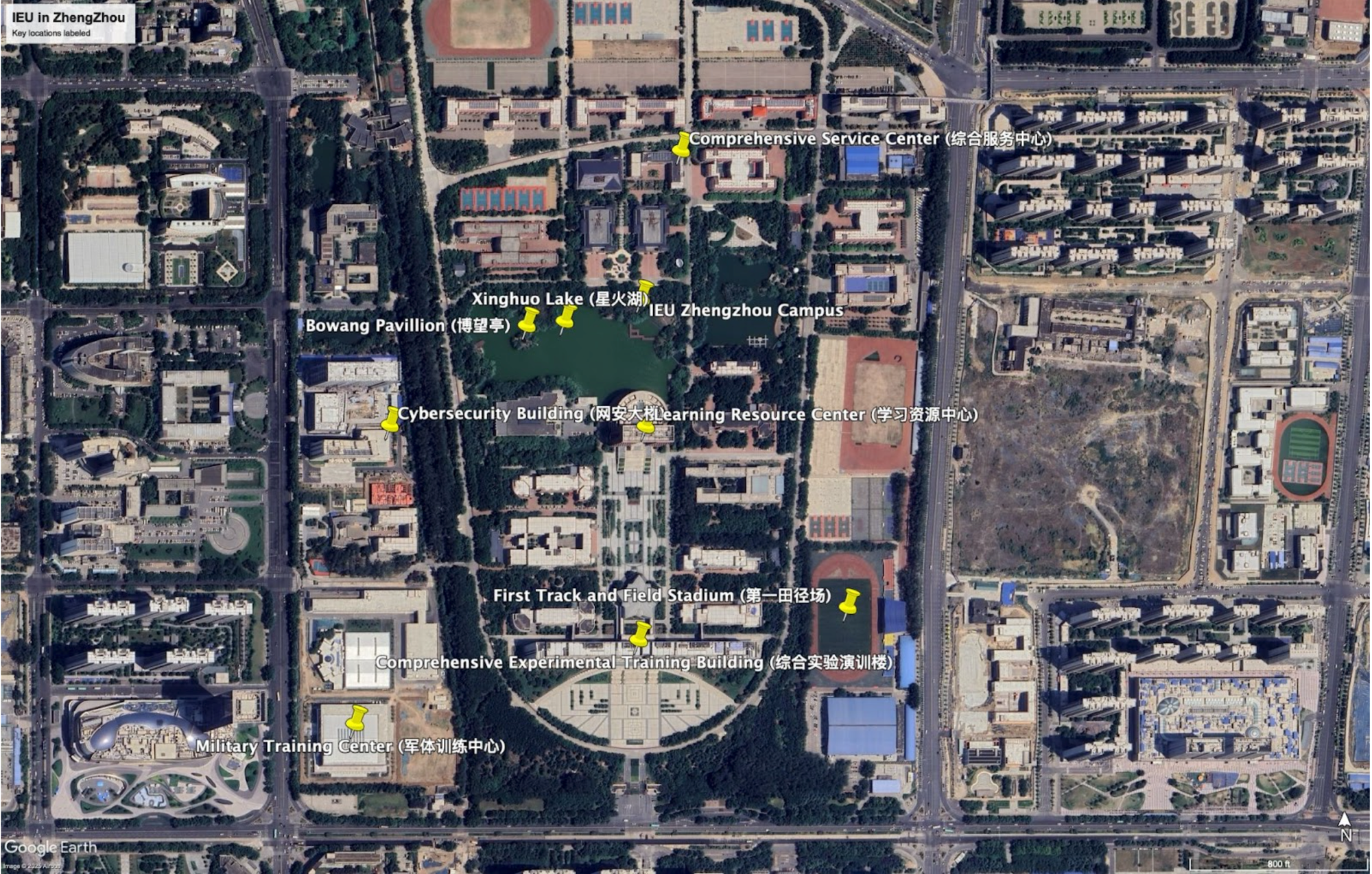
The PLA Goes Back to School: Mapping New Developments in China’s Military Cyber Education System
It’s September, which means beginning the ritual of back-to-school season. That ritual doesn’t just apply to kids with backpacks—military cadets across the world are heading back into classrooms too. In China, cyber-track cadets are heading into classrooms that don’t look quite like last year’s. The

Margin Research Bug Bounty Program
Margin Research is pleased to announce the launch of its bug bounty program. Specifically Margin is putting a bounty on spotted lanternflies (pictured below). Spotted lanternflies are an invasive species that feed on crops including grapes, stone fruit, and soybeans. Enter to win exclusive Margin Research Bug Bounty Program merch

Cyber Militias Redux: Or, "Why Your Boss Might Also Be Your Platoon Leader in China"
Recently, Margin published a piece on China’s cyber militias and how they fit into their broader defense strategy. It’s gotten a very positive reception overall, but there’s one question that’s come up more than once, both in chats I’ve had and in other corners of

The Fake IT Worker Triangle: Pyongyang, Moscow, and Beijing
As North Korea sends thousands of troops to Russia, to aid with Russia’s full-on war on Ukraine, there is a concerning development in relations between Russia, North Korea, and China—Russia and China’s role in North Korean operations against Western tech firms. CoinDesk published a story on October

You Can’t Spell WebRTC without RCE - Part 3
This is the third and final part of our blog post series on Signal and iOS exploitation via the insertion of synthetic vulnerabilities. Part one explored Signal and WebRTC, detailing the injected vulnerabilities and the process of adding them. In part two we leverage these vulnerabilities to exfiltrate the Signal

You Can't Spell WebRTC without RCE - Part 2
This is the second part in our three-part series on exploring WebRTC, Signal-iOS, and iOS exploitation. The first post in this series surveyed WebRTC's implementation of various protocols, injected arbitrary read and arbitrary write vulnerabilities, and set up a research environment to trigger the vulnerabilities. This post continues

You Can't Spell WebRTC without RCE - Part 1
Injecting and Exploiting Synthetic Remote Vulnerabilities to explore Signal-iOS and WebRTC It’s another average Friday morning and my iPhone shows 705 unread Signal messages. Signal has not completely supplanted my use of iMessage, but it does dominate communications with industry peers and privacy-conscious friends. If you are a cybersecurity

Disassembling Dalvik
In this post, we announce the release of a small library for disassembling Dalvik bytecode. This serves as a foundation for building static analysis tooling for Android applications and system services in Rust. Read on for an example graphview application, or just check out the crate’s source and documentation